What do you think of when you hear the phrase "dark web?" Chances are, if you've been conditioned by the media, you probably think it's some kind of elite underground version of the world wide web where the only things to happen there are some of the worst crimes imaginable - drug dealing, CSAM, hacking, murder, and fraud.
But this is only a small but vocal part of the "dark web." In reality, most of the content on the "dark web" you'll come across takes the form of personal blogs, frontends to popular web services, other services like email providers, and of course, the occasional bit of piracy (which is hardly a crime - the real criminal is Hollywood, but that's a blog post for another day).
But to really understand the "dark web," we need to look at the protocols that make it up.
First up is Tor, easily the most popular protocol that makes up the "dark web." It's a protocol maintained by the Tor Project, and was initially released unto the world in 2002. It operates on a relay system, where the main computer sends its request, and that request is run through 3 randomly chosen relays: the guard or entry relay, the middle relay, and the exit relay. The guard relay takes the request and sends it to the middle relay, which sends it to the exit relay, which sends it to the server you're trying to contact. The server will then process the request, and send back the according information in the same way, again through 3 random relays.
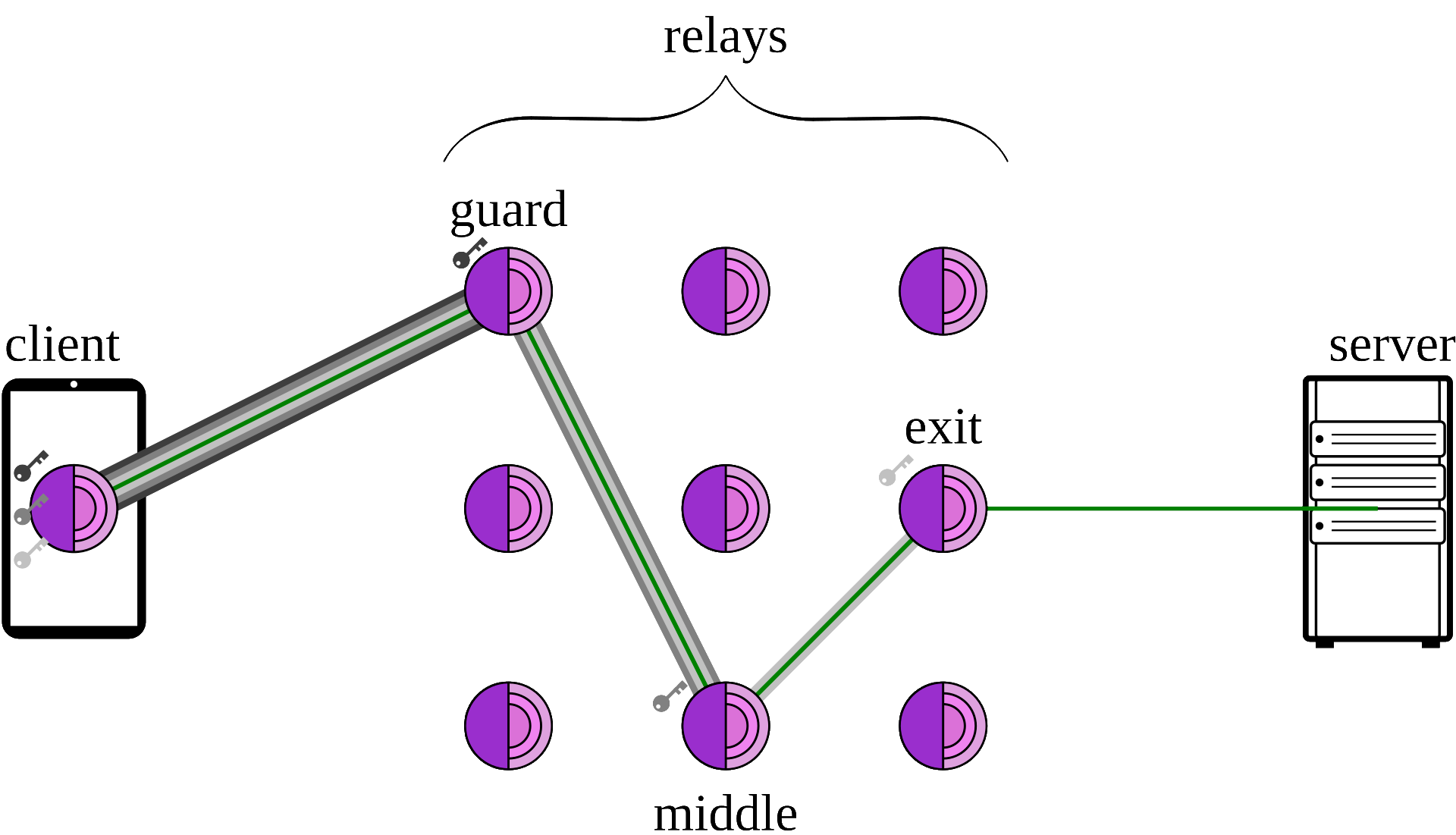
Tor is unique in that it can be used both as a proxy over the clearnet (i.e. the regular web) while also being able to make use of special hidden services (called .onion domains, or onionsites) only accessible on Tor. These hidden services can have basically all the functions of a regular website, and surprisingly, a number of popular websites offer .onion services, including Reddit, DuckDuckGo, The New York Times, the British Broadcasting Corporation (BBC), Mullvad VPN, Proton Mail, and formerly Twitter. In regards to overall popularity and overall security, Tor is the default choice for most people using the "dark web," which makes it the most popular choice, but that popularity has led to advancements in authorities being able to crack the security of the network, something that, while it does reduce crime, is bad for the overall userbase, illicit or not, as many people use Tor to circumvent censorship in oppressive nations, so that they might access valuable information. Tor is also pretty widely used in the world of investigative journalism, as it keeps the journalist safe in their efforts to uncover information if they're working on a dangerous case.
The next major network that makes up the "dark web" is I2P, short for the Invisible Internet Protocol. I2P operates on a peer-to-peer network, meaning that anyone using the network is a peer, meaning they contribute bandwidth to the network. This stands in contrast to Tor, where many people use the network, but not everyone contributes to the network by running their own relay (which is a risky task depending on what type of relay you choose to run - running an exit relay can put you in trouble with the law since that's the relay that exposes any incriminating information to the server it's requesting information from). I2P generally cannot be used as a proxy over the clearnet unless you configure an outproxy on the I2P network (the most popular of which is exit.stormycloud.i2p) which can provide clearnet sites to the I2P user, albeit at the cost of speed (outproxies are slow as FUCK). I2P, being a peer-to-peer network, is especially well-suited to torrenting, which is one of the main selling points of I2P over Tor, which does not allow torrenting over the network. However, I2P generally cannot make use of clearnet torrents, instead having its own BitTorrent trackers exclusive to the network, though intermingling with the clearnet is possible, but slow. I2P, due to not being as popular as Tor, and as a side-effect of being a P2P protocol, is generally more secure, making it ideal for someone who wants tons of security. Generally most of the content you'll find on I2P is completely legal, and many folks run personal blogs and other cool services over the network - but of course, there's always illegal shit no matter how much cool shit there is, it's just less common on I2P.
The final "dark web" network I wanna touch on is Hyphanet, formerly yet still colloquially known as Freenet. It's another peer-to-peer protocol, like I2P, but it operates on a much more complex implementation, making use of a decentralized data store distributed over the entire network as a means of sharing encrypted information. Individual domains like .com, .onion, or .i2p don't exist in Freenet/Hyphanet, instead taking the form of super-long hashed keys that you are not gonna be able to type from memory. The Freenet/Hyphanet developers insist that the network can only work and have true freedom of speech via absolute anonymity, meaning that the illicit content is more plentiful on Freenet/Hyphanet, and is easier to find, but is also more easily avoided. The devs believe that Freenet/Hyphanet's positive uses, such as circumventing oppressive censorship to access valuable information, and maintaining maximum security, far outweigh the negative uses, such as hosting illegal content. Freenet/Hyphanet operates in two ways, opennet and darknet mode. Opennet mode is the default when you start using the network, and doesn't have the utmost security, but is servicable. The darknet mode is manually enabled by choosing other users of the network that you know and trust (ideally IRL) to handle your traffic. This works both ways. While opennet connections are easy and simple, darknet connections are ridiculously secure, and in many cases oppressive authorities won't even be able to detect that you're using the network at all, but it's harder to find users you trust and set it up.
Now that we've established a few of the protocols that make up the "dark web," let's actually talk about the appeal and use cases for it. As stated earlier, much of the content you'll find is personal blogs, frontends to popular web services, a number of popular websites, and various other cool services. Of course, on the "dark web" you'll also find a lot of illegal content, thanks to the allure of anonymity and security, which speaks moreso about the warped aspects of human nature than about the legal encumberments of the networks themselves. Of course, the prevalence of illegal content on the "dark web" has a certain mystique about it, which is very heavily touched upon by popular media, which generally treats the "dark web" as an all-illegal super-dangerous no-mans-land than a legitimate means of accessing information. What many people fail to realize about the "dark web" however, is that its amount of illegal content isn't that much more than that which is present on the clearweb. Don't get it twisted; there's plenty of illegal shit on the clearweb, but it's not as interesting to say a human trafficking ring was busted on Craigslist than to say a human trafficking ring was busted on the "dark web." In reality, as long as you're careful with what you click on, you can use the "dark web" very productively and not have to worry about getting your door and face kicked in by the feds. It just takes discretion and a realization that it's not as bad as it's been made out to be. This teaching can also be applied to the clearweb as well.
Hopefully you learned something.
----------Back to the blog index----------